
AWS IAM Role Setup for EC2 Access
Prepared for: Cloud Bridge Marlow Technical Assessment | By: Anwer Sadath Abdhul Muttaliff

Prepared for: Cloud Bridge Marlow Technical Assessment | By: Anwer Sadath Abdhul Muttaliff
This project demonstrates secure IAM role configuration for EC2 instances, following AWS best practices. It showcases my ability to implement least-privilege access controls - a critical requirement for Cloud Support Engineers at Cloud Bridge.
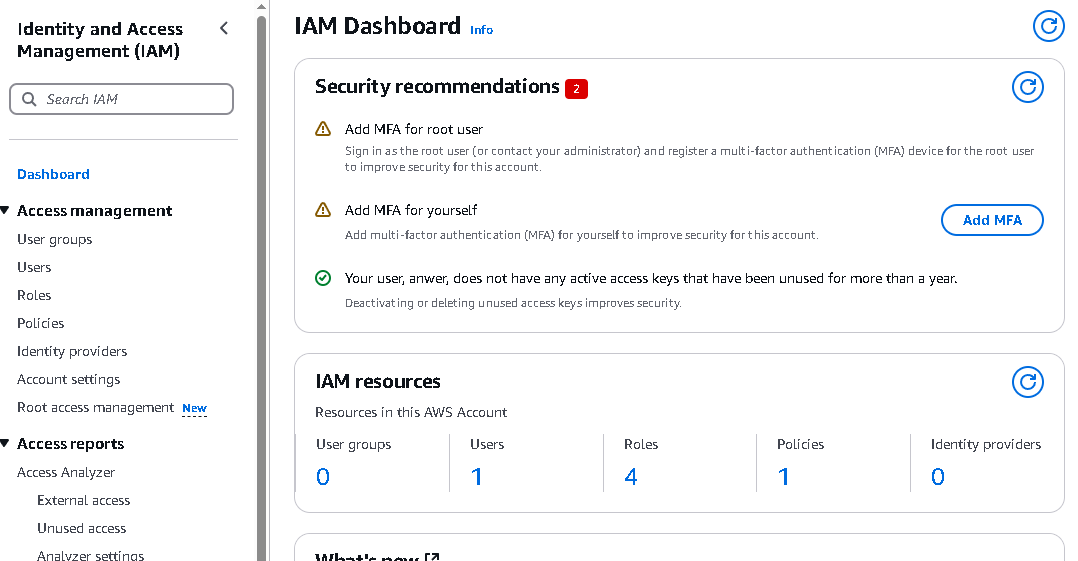
1. Click "Roles" in the left navigation
2. Click "Create Role" (top right)
3. Select "AWS service" as trusted entity type
4. Choose "EC2" as the service that will use this role
5. Click "Next" to proceed to permissions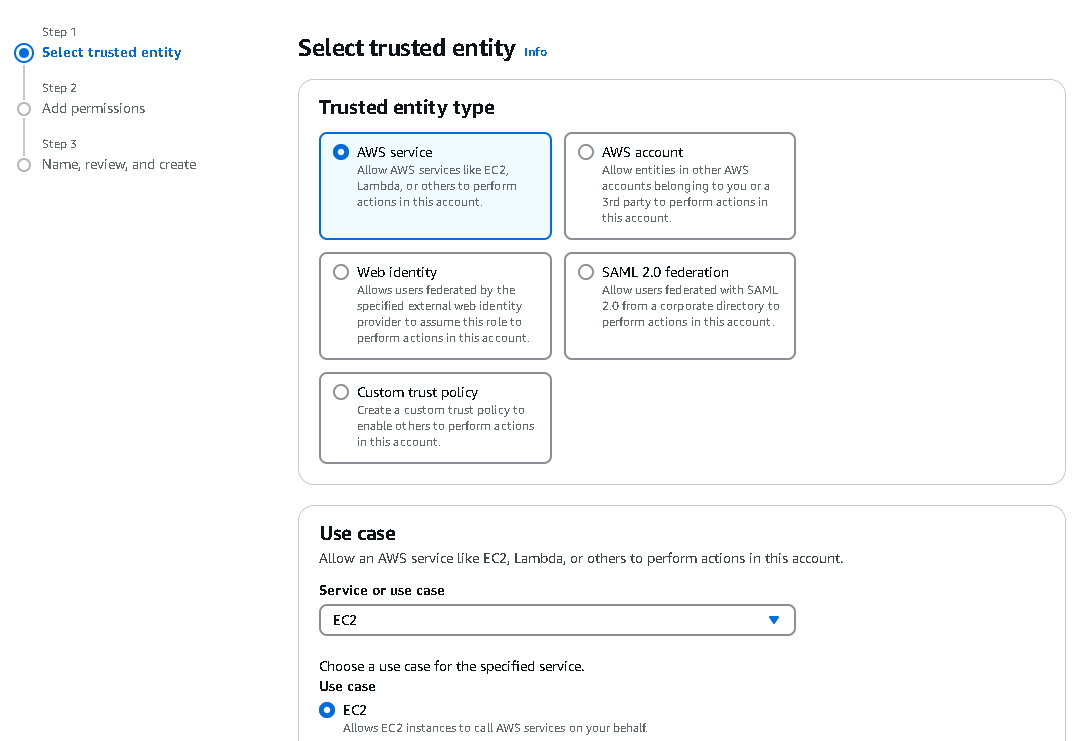
Following the principle of least privilege:
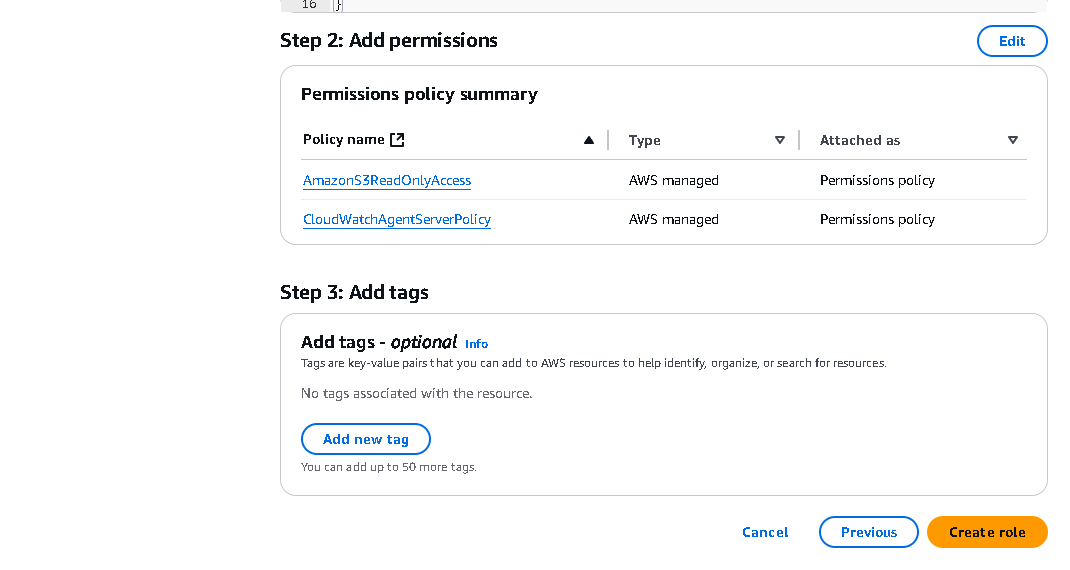
1. Name: "CloudBridge-EC2-Role"
2. Description: "Allows EC2 to access S3 and CloudWatch"
3. Review all settings
4. Click "Create Role"Security Note: Avoid using wildcard permissions (*) in production environments.
1. Navigate to EC2 Dashboard
2. Select your instance
3. Click "Actions" > "Security" > "Modify IAM Role"
4. Select your newly created role
5. Click "Update IAM Role"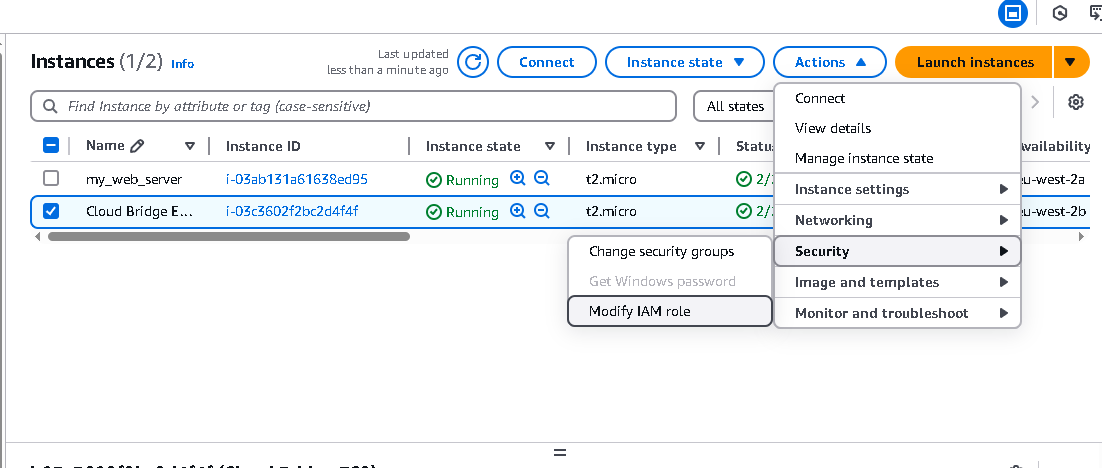
1. SSH into your EC2 instance
2. Run: aws sts get-caller-identity
3. Verify output shows correct IAM Role
4. Check permissions with test commands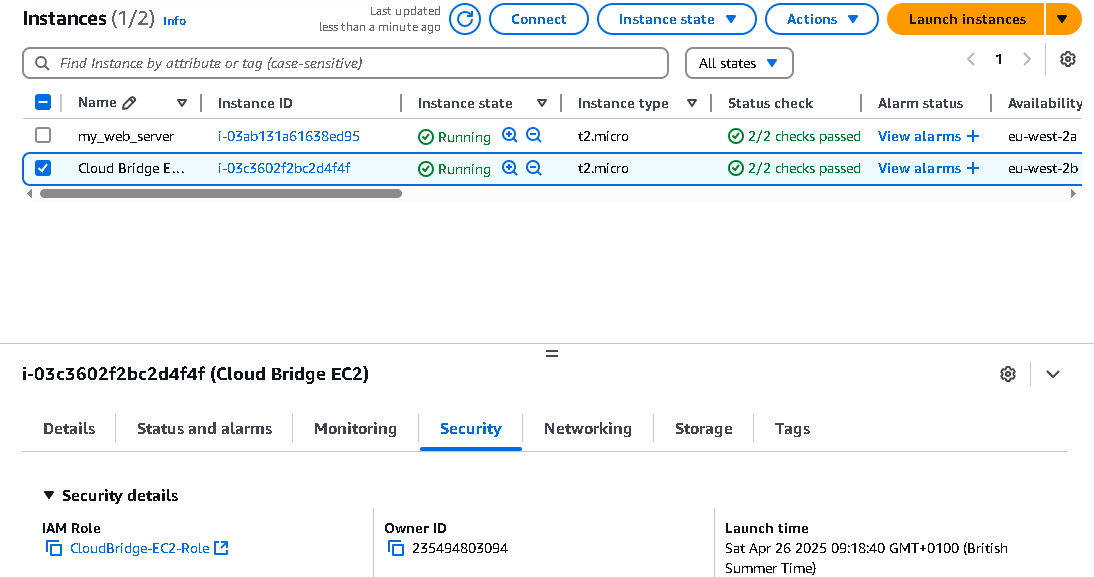
This demonstration shows my ability to implement secure AWS IAM configurations following Cloud Bridge Marlow's security standards.
Back to Top Back to Home